Mobile Application Testing
Indeses: Enhancing Your Mobile Application Testing Journey
Mobile Application VAPT (Vulnerability Assessment and Penetration Testing) is a comprehensive security testing process conducted on mobile applications to identify and address security vulnerabilities and potential threats. Just like web application VAPT, mobile application VAPT is crucial for ensuring the security of mobile apps, protecting sensitive user data, and minimizing the risk of unauthorized access or breaches
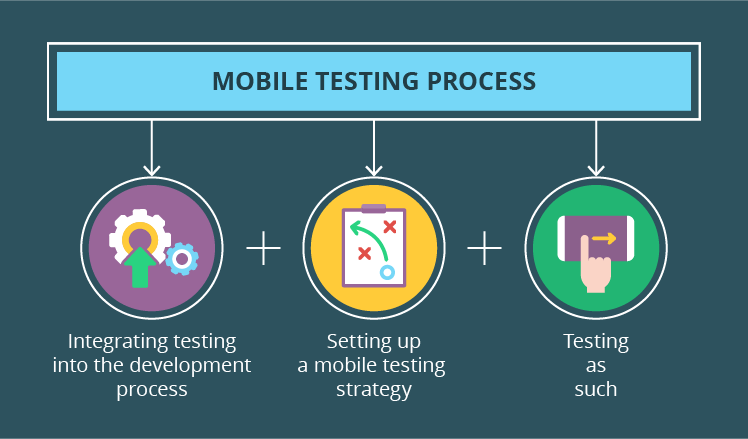
The process of Mobile Application VAPT involves the following key steps
Mobile Application VAPT is essential for maintaining the security and trustworthiness of mobile apps, especially since mobile devices often handle sensitive personal data. By conducting thorough VAPT assessments, developers and organizations can identify vulnerabilities early in the development lifecycle and minimize the risk of security breaches that could have serious consequences for users and the business.

Requirement Gathering and Scoping
Understand the mobile application's functionalities, platforms (iOS, Android, etc.), and intended user base. Determine the scope of the VAPT process and define the testing methodologies to be employed

Threat Modeling
Analyze potential threats and attack vectors that the mobile app might be susceptible to. This involves identifying potential weaknesses, vulnerabilities, and areas that require special attention.
.jpg)
Vulnerability Assessment (VA)
Similar to web applications, vulnerability assessment focuses on identifying potential vulnerabilities within the mobile application. The main steps involved in the Vulnerability Assessment phase include:
- Static Analysis: Review the application's source code and binaries to identify vulnerabilities such as insecure coding practices, hardcoded credentials, and insecure storage
- Dynamic Analysis: Run the application in controlled environments to simulate real-world scenarios. Monitor how the app behaves during 15 runtime to identify runtime vulnerabilities, data leakage, and unauthorized actions
- Network Analysis: Analyze the network traffic generated by the app to identify any insecure communication, data leaks, or potential man-in-the-middle attacks.
.jpg)
Penetration Testing (PT)
Penetration Testing involves actively attempting to exploit identified vulnerabilities to assess the extent of potential damage and compromise. The main steps involved in the Penetration Testing phase include:
- Authentication and Authorization Testing: Verify that authentication and authorization mechanisms are secure and cannot be bypassed.
- Data Leakage Testing: Check for sensitive data exposure, including unintentional sharing of user information.
- Encryption Testing: Evaluate the encryption methods used to protect data in transit and at rest.
- Reverse Engineering: Analyze the app's code and binaries to uncover vulnerabilities that might not be apparent through static analysis alone.
- Secure Configuration Testing: Ensure the app adheres to best practices in terms of security configurations.

Reporting and Remediation
Compile the findings from the vulnerability assessment and penetration testing phases into a comprehensive report. The report should include detailed explanations of identified vulnerabilities, their severity levels, potential impacts, and recommendations for remediation.

Re-Testing and Validation
After the identified vulnerabilities are addressed and security patches are applied, the application should undergo re-testing to ensure 16 that the issues have been properly resolved and that no new vulnerabilities have been introduced
OWASP TOP 10 FOR MOBILE APPLICATIONS
The OWASP Top 10 for Mobile Applications is a list of the ten most critical security risks faced by mobile applications. Similar to the OWASP Top 10 for web applications, this list is created by the Open Web Application Security Project (OWASP) to help developers, security professionals, and organizations understand and address the most prevalent security vulnerabilities that affect mobile apps.
-
 Improper Platform Usage: This risk refers to issues that arise due to improper
use of the mobile platform's security features. Developers should understand and
properly implement platform security mechanisms such as encryption,
permissions, and secure data storage.
Improper Platform Usage: This risk refers to issues that arise due to improper
use of the mobile platform's security features. Developers should understand and
properly implement platform security mechanisms such as encryption,
permissions, and secure data storage.
-
 Insecure Data Storage: Sensitive data stored on a mobile device can be
compromised if not properly protected. This risk emphasizes the need to securely
store sensitive data, including passwords, personal information, and financial
data
Insecure Data Storage: Sensitive data stored on a mobile device can be
compromised if not properly protected. This risk emphasizes the need to securely
store sensitive data, including passwords, personal information, and financial
data
-
 Insecure Communication: Mobile apps often communicate with servers or
other apps. If communication is not properly secured through encryption and
other measures, attackers can intercept or manipulate the data being
transmitted.
Insecure Communication: Mobile apps often communicate with servers or
other apps. If communication is not properly secured through encryption and
other measures, attackers can intercept or manipulate the data being
transmitted.
-
 Insecure Authentication: Weak authentication mechanisms can lead to
unauthorized access. Developers must ensure that proper authentication
methods are used and that sensitive actions can't be performed without proper
authentication.
Insecure Authentication: Weak authentication mechanisms can lead to
unauthorized access. Developers must ensure that proper authentication
methods are used and that sensitive actions can't be performed without proper
authentication.
-
 Insufficient Cryptography: Cryptographic weaknesses can lead to the
compromise of sensitive data and communications. Developers should use
21
strong encryption algorithms and implement cryptography properly to avoid
vulnerabilities.
Insufficient Cryptography: Cryptographic weaknesses can lead to the
compromise of sensitive data and communications. Developers should use
21
strong encryption algorithms and implement cryptography properly to avoid
vulnerabilities.
-
 Insecure Authorization: Authorization vulnerabilities can allow unauthorized
users to access restricted functionality or data. Proper authorization checks
should be in place to prevent unauthorized actions.
Insecure Authorization: Authorization vulnerabilities can allow unauthorized
users to access restricted functionality or data. Proper authorization checks
should be in place to prevent unauthorized actions.
-
 Client Code Quality: Insecure code in the mobile app itself can lead to
vulnerabilities. Poorly written code can be exploited by attackers to gain
unauthorized access or control over the app
Client Code Quality: Insecure code in the mobile app itself can lead to
vulnerabilities. Poorly written code can be exploited by attackers to gain
unauthorized access or control over the app
-
 Code Tampering: Attackers can tamper with the code of a mobile app to modify
its behavior or introduce malicious code. Implementing anti-tampering measures
is crucial to prevent unauthorized modifications.
Code Tampering: Attackers can tamper with the code of a mobile app to modify
its behavior or introduce malicious code. Implementing anti-tampering measures
is crucial to prevent unauthorized modifications.
-
 Reverse Engineering: Mobile apps can be reverse-engineered to understand
their inner workings or identify vulnerabilities. Proper obfuscation and security
mechanisms should be used to deter reverse engineering
Reverse Engineering: Mobile apps can be reverse-engineered to understand
their inner workings or identify vulnerabilities. Proper obfuscation and security
mechanisms should be used to deter reverse engineering
-
 Extraneous Functionality: Unused or unnecessary functionality in an app can
introduce vulnerabilities. Attackers may exploit these features to compromise the
app's security.
Extraneous Functionality: Unused or unnecessary functionality in an app can
introduce vulnerabilities. Attackers may exploit these features to compromise the
app's security.
Our Process: Android App Development
We Uphold Utmost Clarity Through Our Project Management Tool.
Project
As soon as we get the project, we go through it properly so that we can fulfill the requirements of our clients.
This is how we make it happen
- Wireframes
- Requirement List
- Milestone Plan
- UI Screens
KT of Project
Our KT planning template consists of the roadmap with the key factors that need to be considered while developing the mobile application. Basically, it comprises the complete project requirements.
Tools
- Android Studio Tool
- Android-IDE
Tools
- Kotlin
- Java
- C
- C++
- Python

Android App Development
Our Android App Development process is transparent and quick, making us a reliable app development company. We create Android apps backed by the most innovative technologies and our wide platform-expertise makes us competent to offer multiple services.
Our team has
- Proficiency in Java Programming
- Know the Value of Good Design
- Expertise in Cross-Platform
- Have a Spatial Reasoning
Testing
Process of Testing
We know that Testing is an essential division of the mobile app development lifecycle. Therefore, to make sure the victorious development of any application, we involve it the different stages of development process i.e. from building the concept to examining the requirements.
- Building APK
- Share APK
- Clients Approval
- Release Of APK
Prerequisites
-

Please share with us the APK file and the IPA file for the application so that we can continue the testing. I have attached two PDF documents, each showing the steps to follow in order to generate a signed APK file and an IPA file for us. If the apps are live on the play store or app store, please share the links with us.
-

Information and credentials about various ‘roles’ in the application and provision dummy/test accounts for each role. This is needed to check for business logic flaws and privilege escalation vulnerabilities.

In preparation for the upcoming audit, we kindly request the completion of essential prerequisites. Firstly, we ask for the creation of a new IAM user in the Cloud Management Console, equipped with read-only permissions for all services. It is crucial to attach the Security Auditor job function to ensure comprehensive access during the audit. Additionally, we request a comprehensive list of all Cloud services currently in use, providing valuable insights into the architecture of your Cloud environment. Lastly, for seamless programmatic access through the AWS CLI, we seek the provision of the Access Key ID and Secret Access Key associated with the newly created IAM user, along with the specified Cloud region. These steps are vital to ensuring a smooth and effective audit process of your Cloud infrastructure.

The cloud assessment is always preferred to be done on production accounts as a standard because we would want to analyze the configurations set in place in the cloud infrastructure handling the latest versions of software, products, or updates pushed live to your users. We further confirm that we do not modify any data on your cloud account, but only read and assess the configurations for each AWS service in use.
Static And Dynamic Testing
Static and dynamic testing are two different approaches to assessing the security of a mobile application. Each approach has its own focus and methodology. Here's an overview of the differences between static and dynamic testing of mobile applications:
Static Testing:
 Focus:
Static testing primarily involves analyzing the application's source code,
binaries, and other artifacts without executing the application itself. It aims to
identify vulnerabilities by examining the code and its potential interactions with
the underlying platform.
Focus:
Static testing primarily involves analyzing the application's source code,
binaries, and other artifacts without executing the application itself. It aims to
identify vulnerabilities by examining the code and its potential interactions with
the underlying platform.
 Methodology: During static testing, security analysts review the source code
and related files to identify coding errors, security flaws, and potential
vulnerabilities. They often use automated tools to assist in this process, which
can detect issues like insecure coding practices, hardcoded credentials, and
other vulnerabilities in the application's codebase.
Methodology: During static testing, security analysts review the source code
and related files to identify coding errors, security flaws, and potential
vulnerabilities. They often use automated tools to assist in this process, which
can detect issues like insecure coding practices, hardcoded credentials, and
other vulnerabilities in the application's codebase.
 Advantages:
Advantages:
- Early Detection: Static testing can identify vulnerabilities at an early stage of development, allowing developers to fix them before the application is deployed.
- In-Depth Analysis: Analysts can perform a thorough examination of the codebase, uncovering intricate vulnerabilities that might be missed through other testing methods.
- No Execution Required: Static testing does not require running the application, making it suitable for finding issues before the app is fully functional.
 Limitations:
Limitations:
- Cannot Detect Runtime Behavior: Static testing doesn't capture how the application behaves when executed, which means it might miss vulnerabilities that only manifest during runtime
- Limited Context: Without executing the app, certain vulnerabilities that depend on user interactions or external factors might not be identified.
Dynamic Testing:
 Focus:
Dynamic testing involves executing the application and observing its
behavior in a controlled environment. It aims to identify vulnerabilities and issues
that arise during the app's runtime execution.
Focus:
Dynamic testing involves executing the application and observing its
behavior in a controlled environment. It aims to identify vulnerabilities and issues
that arise during the app's runtime execution.
 Methodology: In dynamic testing, the app is run on actual devices, emulators, or
simulators. Security analysts interact with the app and use automated tools to
simulate different usage scenarios, exploring how the app responds and
identifying potential security flaws.
Methodology: In dynamic testing, the app is run on actual devices, emulators, or
simulators. Security analysts interact with the app and use automated tools to
simulate different usage scenarios, exploring how the app responds and
identifying potential security flaws.
 Advantages:
Advantages:
- Real-World Behavior: Dynamic testing captures the actual behavior of the application during runtime, helping identify issues that may only surface when the app is in use.
- User Interaction: Dynamic testing can identify vulnerabilities that result from user actions, such as data leakage during certain transactions
- Vulnerability Validation: Dynamic testing can help verify if the vulnerabilities identified during static testing can be practically exploited.
 Limitations:
Limitations:
- Limited to Known Scenarios: Dynamic testing depends on the test scenarios defined by analysts, which may not cover all possible real-world usage scenarios.
- May Miss Code-Level Flaws: Certain vulnerabilities originating from the source code might not be identified during dynamic testing if they don't manifest during runtime.
In summary, static testing focuses on analyzing the code and artifacts without executing the application, while dynamic testing involves running the app and observing its behavior during runtime. Both approaches are valuable and can provide different perspectives on the security of a mobile application. Combining both static and dynamic testing in a comprehensive security assessment strategy is often recommended to ensure thorough coverage of potential vulnerabilities.
