Network Testing
Indeses: Enhancing Your Network Testing Journey
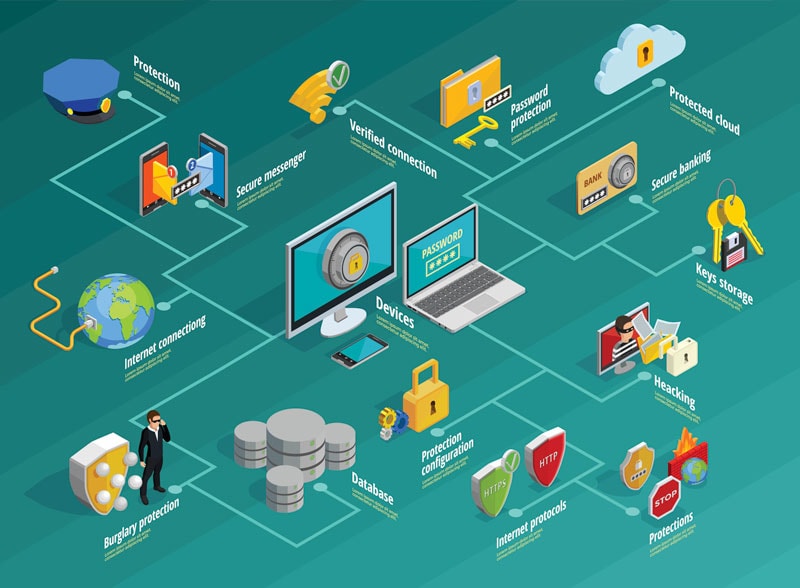
Network Vulnerability Assessment and Penetration Testing (Network VAPT) is a comprehensive process conducted to identify and address security vulnerabilities in an organization's network infrastructure. This assessment aims to proactively identify weak points and potential security risks within the network, helping organizations strengthen their overall security posture and prevent potential cyberattacks.

Top 10 Vulnerabilities For Networks
Network vulnerabilities are weaknesses or security flaws in a network infrastructure that could potentially be exploited by attackers to compromise the confidentiality, integrity, or availability of network resources and data. The specific vulnerabilities that are most critical can vary depending on the network's architecture, technologies, and configurations. Here's a list of common network vulnerabilities that organizations should be aware of

Weak or Default Passwords
Devices and services configured with weak or default passwords are vulnerable to unauthorized access. Attackers can exploit this by using brute force attacks or password-guessing techniques
Unpatched Systems
Failing to apply security patches and updates can leave systems vulnerable to known vulnerabilities that attackers can exploit to gain unauthorized access or launch attacks.

Misconfigured Firewalls
Improperly configured firewalls can allow unauthorized traffic to pass through, compromising the network's security posture and exposing internal resources to external threats

Insecure Network Protocols
Legacy and insecure protocols like Telnet, SNMPv1, and SMBv1 lack encryption and strong authentication, making them susceptible to eavesdropping and attacks.

Open Ports and Services
Unused or unnecessary open ports and services provide potential entry points for attackers. These ports should be closed or properly secured to prevent unauthorized access.
Lack of Network Segmentation
Networks without proper segmentation can allow attackers to move laterally across the environment once they gain access to a single system, increasing the potential impact of a breach.

Phishing and Social Engineering
Human error is a significant vulnerability. Phishing attacks and social engineering tactics can trick users into revealing sensitive information or installing malicious software.
 Attacks.jpg)
Denial of Service (DoS) Attacks
DoS attacks overwhelm network resources, rendering services unavailable. Organizations should implement proper traffic filtering and rate limiting to mitigate such attacks

Insufficient Network Monitoring
Inadequate monitoring makes it difficult to detect unauthorized activities or breaches. Organizations should implement intrusion detection and prevention systems (IDS/IPS) and analyze network logs
Wireless Network Vulnerabilities:
Insecurely configured or unsecured wireless networks can expose organizations to unauthorized access, eavesdropping, and man-in-the-middle attacks.
It's important to note that network vulnerabilities can differ based on the organization's industry, network architecture, and technology stack. Regular network assessments, vulnerability scanning, penetration testing, and adherence to security best practices are essential to identifying and addressing these vulnerabilities effectively. Additionally, staying informed about emerging threats and keeping up-to-date with security patches and updates is crucial for maintaining a secure network environment
Our Process: Android App Development
We Uphold Utmost Clarity Through Our Project Management Tool.
Project
As soon as we get the project, we go through it properly so that we can fulfill the requirements of our clients.
This is how we make it happen
- Wireframes
- Requirement List
- Milestone Plan
- UI Screens
KT of Project
Our KT planning template consists of the roadmap with the key factors that need to be considered while developing the mobile application. Basically, it comprises the complete project requirements.
Tools
- Android Studio Tool
- Android-IDE
Tools
- Kotlin
- Java
- C
- C++
- Python

Android App Development
Our Android App Development process is transparent and quick, making us a reliable app development company. We create Android apps backed by the most innovative technologies and our wide platform-expertise makes us competent to offer multiple services.
Our team has
- Proficiency in Java Programming
- Know the Value of Good Design
- Expertise in Cross-Platform
- Have a Spatial Reasoning
Testing
Process of Testing
We know that Testing is an essential division of the mobile app development lifecycle. Therefore, to make sure the victorious development of any application, we involve it the different stages of development process i.e. from building the concept to examining the requirements.
- Building APK
- Share APK
- Clients Approval
- Release Of APK
Here's a breakdown of Network VAPT
Network VAPT is an ongoing process that needs to be periodically performed to address new vulnerabilities that arise due to changes in technology, updates, and emerging threats. It is an integral part of an organization's cybersecurity strategy to ensure the confidentiality, integrity, and availability of network resources and sensitive information
 Challenges of Network VAPT:
This is the initial phase of Network VAPT, where the
focus is on identifying vulnerabilities within the network infrastructure. Vulnerability
assessment involves using various tools and techniques to scan the network for known
vulnerabilities, misconfigurations, and weak points. It typically includes the following
steps:
Challenges of Network VAPT:
This is the initial phase of Network VAPT, where the
focus is on identifying vulnerabilities within the network infrastructure. Vulnerability
assessment involves using various tools and techniques to scan the network for known
vulnerabilities, misconfigurations, and weak points. It typically includes the following
steps:
- Scope Complexity: Modern networks are complex, comprising various devices, endpoints, and technologies that need to be thoroughly tested
- Potential Disruptions: Penetration testing could potentially disrupt network operations if not properly planned.
- False Positives: Automated tools might produce false positives, requiring manual verification and validation.
 Benefits of Network VAPT:
Benefits of Network VAPT:
- Early Detection of Vulnerabilities: Identifying vulnerabilities before they are exploited by attackers
- Enhanced Security Posture: Implementing remediation measures based on assessment findings to strengthen network security.
- Risk Reduction: Reducing the risk of cyberattacks, data breaches, and unauthorized access
- Regulatory Compliance: Meeting compliance requirements for network security assessments.
 Vulnerability Assessment:
This is the initial phase of Network VAPT, where the
focus is on identifying vulnerabilities within the network infrastructure. Vulnerability
assessment involves using various tools and techniques to scan the network for known
vulnerabilities, misconfigurations, and weak points. It typically includes the following
steps:
Vulnerability Assessment:
This is the initial phase of Network VAPT, where the
focus is on identifying vulnerabilities within the network infrastructure. Vulnerability
assessment involves using various tools and techniques to scan the network for known
vulnerabilities, misconfigurations, and weak points. It typically includes the following
steps:
- Network Discovery: Identifying all devices, servers, and endpoints connected to the network.
- Vulnerability Scanning: Automated tools are used to scan the network for known vulnerabilities in hardware, software, and configurations
- Assessment of Misconfigurations: Identifying incorrect or insecure network configurations that can lead to vulnerabilities.
 Penetration Testing:
Penetration testing, often referred to as ethical hacking, goes a
step further by simulating real-world attacks on the network to determine if
vulnerabilities can be exploited. Penetration testing involves controlled attempts to
compromise the network's security and access sensitive information. It includes:
Penetration Testing:
Penetration testing, often referred to as ethical hacking, goes a
step further by simulating real-world attacks on the network to determine if
vulnerabilities can be exploited. Penetration testing involves controlled attempts to
compromise the network's security and access sensitive information. It includes:
- Active Exploitation: Attempting to exploit identified vulnerabilities to gain unauthorized access, escalate privileges, or perform other malicious activities.
- Testing Defenses: Assessing the effectiveness of security controls, such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS)
- Reporting Exploitable Vulnerabilities: Documenting vulnerabilities that were successfully exploited and providing recommendations for remediation
 Reporting and Remediation:
After completing the vulnerability assessment and
penetration testing phases, a detailed report is generated. This report lists all identified
vulnerabilities, their severity levels, potential impacts, and recommendations for
remediation. The organization's IT and security teams can then use this report to
prioritize and address vulnerabilities.
Reporting and Remediation:
After completing the vulnerability assessment and
penetration testing phases, a detailed report is generated. This report lists all identified
vulnerabilities, their severity levels, potential impacts, and recommendations for
remediation. The organization's IT and security teams can then use this report to
prioritize and address vulnerabilities.
Dynamic Testing:
 Focus:
Dynamic testing involves executing the application and observing its
behavior in a controlled environment. It aims to identify vulnerabilities and issues
that arise during the app's runtime execution.
Focus:
Dynamic testing involves executing the application and observing its
behavior in a controlled environment. It aims to identify vulnerabilities and issues
that arise during the app's runtime execution.
 Methodology: In dynamic testing, the app is run on actual devices, emulators, or
simulators. Security analysts interact with the app and use automated tools to
simulate different usage scenarios, exploring how the app responds and
identifying potential security flaws.
Methodology: In dynamic testing, the app is run on actual devices, emulators, or
simulators. Security analysts interact with the app and use automated tools to
simulate different usage scenarios, exploring how the app responds and
identifying potential security flaws.
 Advantages:
Advantages:
- Real-World Behavior: Dynamic testing captures the actual behavior of the application during runtime, helping identify issues that may only surface when the app is in use.
- User Interaction: Dynamic testing can identify vulnerabilities that result from user actions, such as data leakage during certain transactions
- Vulnerability Validation: Dynamic testing can help verify if the vulnerabilities identified during static testing can be practically exploited.
 Limitations:
Limitations:
- Limited to Known Scenarios: Dynamic testing depends on the test scenarios defined by analysts, which may not cover all possible real-world usage scenarios.
- May Miss Code-Level Flaws: Certain vulnerabilities originating from the source code might not be identified during dynamic testing if they don't manifest during runtime.
